Keycase: Self-Hostable Cloud Based Password Manager

Keycase is a browser based, self-hostable cryptographic password manager. It is a chrome extension that lets you encrypt and store passwords securely on firebase.
The passwords are encrypted at rest. So only the user's browser is able to decrypt them. Even firebase administrators with full database access cannot decrypt the contents stored.
This is because all user data is encrypted with a personal RSA key (unique to each user). This RSA key is itself encrypted and stored along with the user record in firebase.
User Interface
Users can sign in to keycase using Google Authentication (Domains configurable).
Keycase requires a master password to decrypt the RSA private key of the user which is stored in the cloud (firebase). This RSA key is used to encrypt and decrypt user passwords.
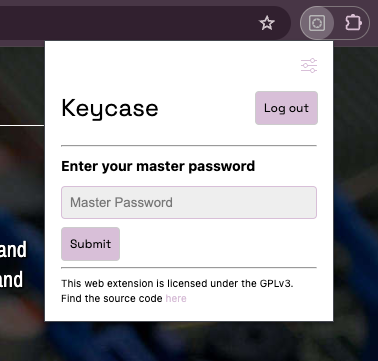
Once the master password is provided, the user is able to decrypt all their passwords stored in the cloud. All cryptography happens on the browser using the Browser Crypto API. This ensures that your data is only ever decrypted on your computer.
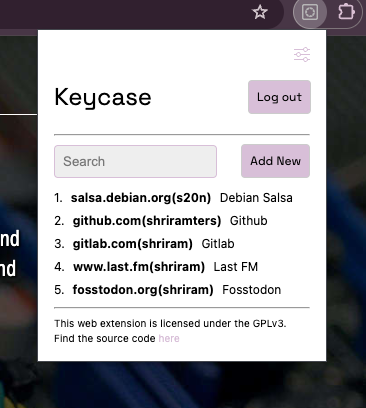
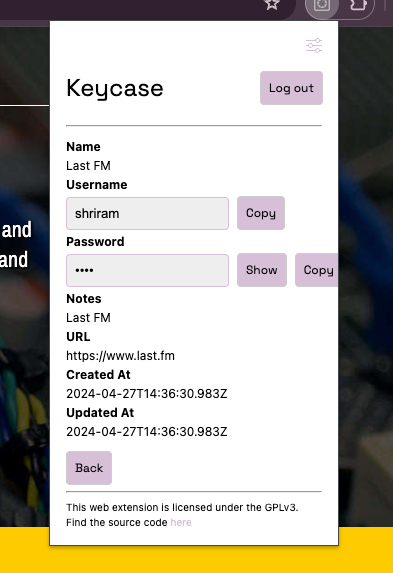
In the above image, we can see the user has five passwords stored. The user can click on any of them to view details and copy the password.
How it works
This is the sequence diagram depicting the workings of keycase. These are the steps involved:
- Login with google authentication
- Receive the AES encrypted RSA private key
- Regenerate the AES key from the user's master password using PBKDF2
- Decrypt the RSA private key with the re-generated AES key
- Use the decrypted RSA private key and the RSA public keys to add, update or delete values from the database.
PBKDF2
Password Based Key Derivation Function 2 is a cryptographic function which can take a string (password) and generate an AES key out of it. This is useful to us as we can then use this AES key to decrypt our RSA key which can then be used to perform our operations.
Why not use the AES key directly
Why do we need an RSA pair when we get a perfectly usable AES key from PBKDF2? If the user wishes to change their master password (for any reason), then we would have had to decrypt all the passwords and re-encrypt them with the new AES key generated from the new password.
Using an RSA keypair eliminates the need for doing all this mass re-encryption since we would only need to re-encrypt the RSA private key with the new AES key.
Database Design
The database for keycase is of a rather simplistic design. We are using Cloud Firestore, which is a Document Database like MongoDB. We have only two collections. viz. Auth and Passwords.
Auth
The Auth collection is used to store the user records.
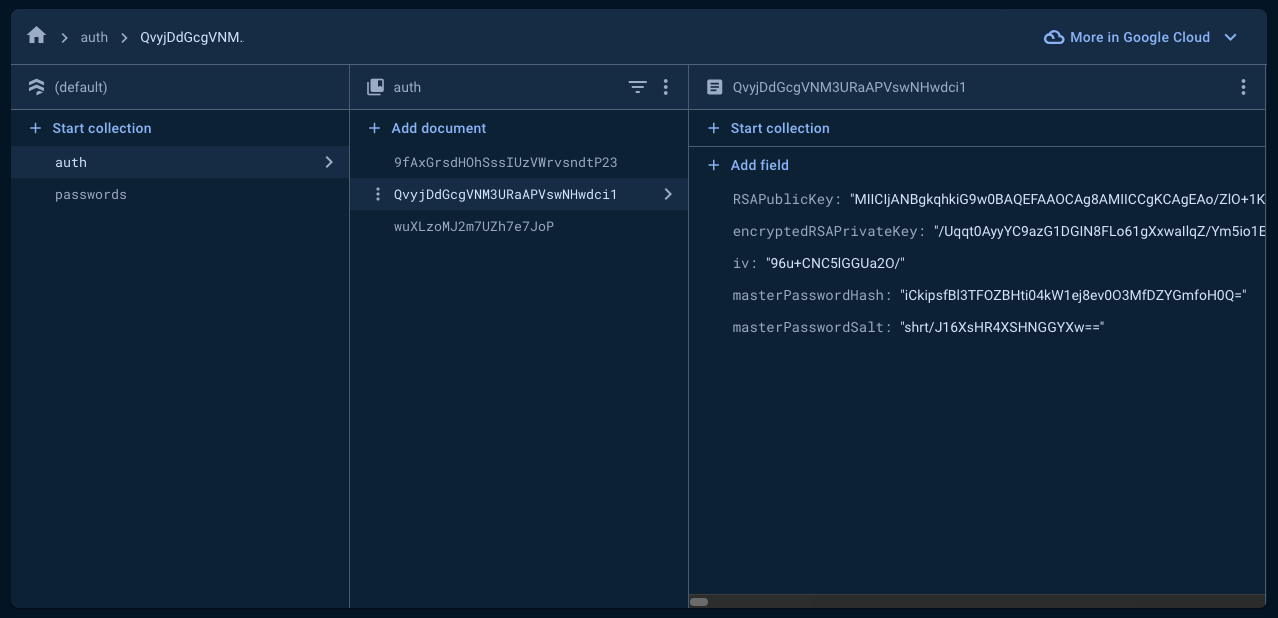
Each document represents one user record. The name of the
document is our user id. In the above image, we can see the user
record of our user with the id QvyjDdGcgVNM3URaAPVswNHwdci1.
Here we're storing the following details of the user:
- RSA Public Key
- AES Encrypted RSA Private Key
- Master Password Hash and Salt
- AES key IV
Passwords
The Passwords collection is used to store all the user passwords.
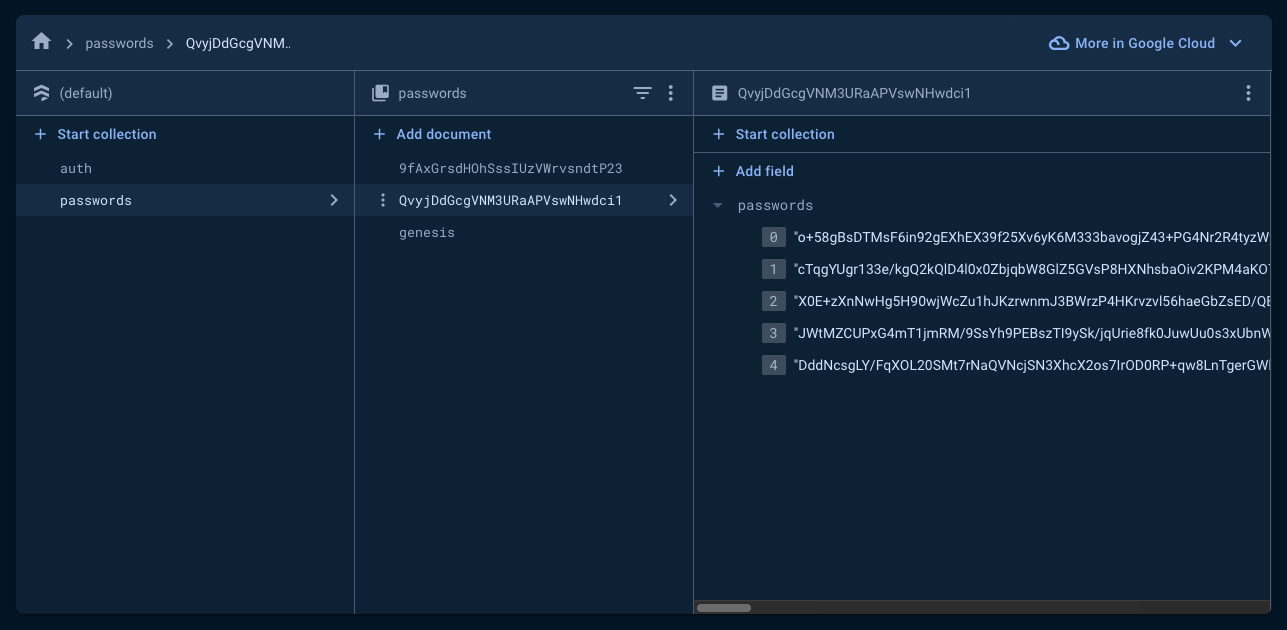
Each user has one document in this collection where their passwords will be stored. In the above image you can see the 5 passwords that were depicted in the earlier screenshot, encrypted and stored as a list.
Closing Words
Keycase is a secure, self hostable password manager for your friends and family. It is by no means perfect. If you find any gaping blunders, please do reach out to me. My contact information is on this website. Please also feel free to contribute your code and make keycase better.
Until Next Time!
